Skicka och ta emot mail med Microsoft 365
Den här guiden beskriver hur Microsoft 365 kan konfigureras för att sätta upp Kundo Mail med Exchange genom användande av Active Directory och Microsofts Graph API. Alla mail bibehålls i er M365-inkorg med den här lösningen - både levererade inkomna mail och alla mail som skickats från Kundo. Om ni önskar automatisk borttagning av mail som hämtats till Kundo och/eller skickade mail: informera oss via support@kundo.se så justerar vi inställningarna för detta.
Förutsättningar
Den här uppsättningen fungerar endast för inkorgar driftade i molnet - Microsoft har tyvärr inte Graph API-stöd för egendriftade "on-premise" inkorgar.
Instruktioner
1. Lägg till en Appregistrering
- Gå till Azure Active Directory i Azure portal
- Gå till Appregistreringar > + Ny registrering
- Fyll i namn: Mail och klicka sedan på Registrera. Ni behöver inte fylla i Omdirigerings-URI
- En sammanfattning för appregistreringen visas nu.
Kopiera Program-ID (klient)/Application (client) ID och Katalog-ID (klientorganisation) / Directory (tenant) ID values.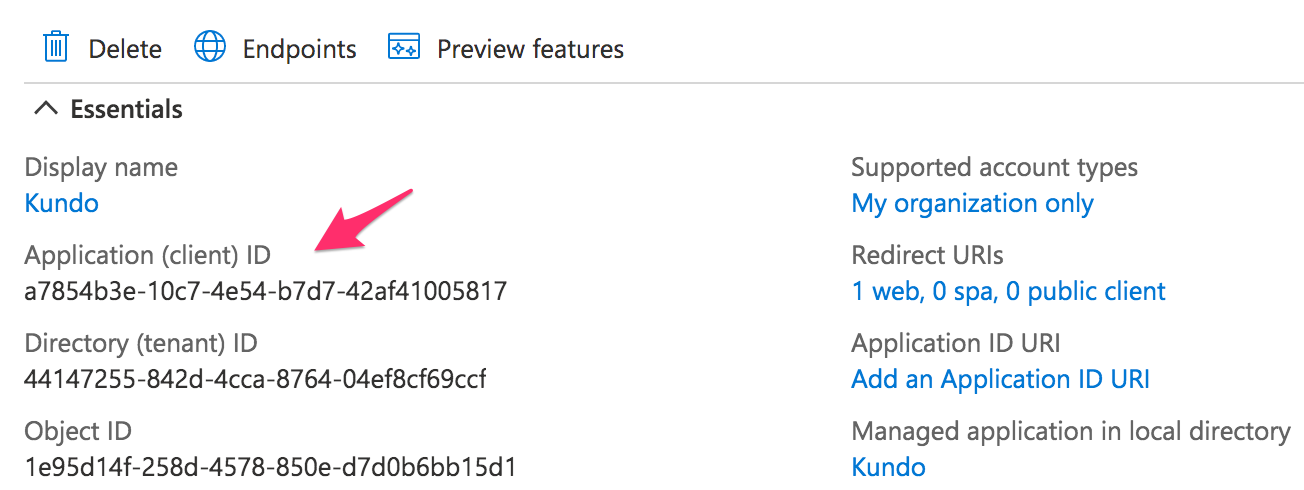
- Gå till Certifikat och hemligheter > Ny klienthemlighet
- Lägg till en ny klienthemlighet och sätt "Upphör att gälla" till 24 månader. Informera vår support på support@kundo.se om ni väljer en kortare period. Kopiera klienthemligheten för användning senare i guiden
- Föregående värden används för att sätta upp integrationen i Kundo under inkorgens inställningar > Skicka & ta emot
- Om ni inte ser följande formulär längst ned på sidan: kontakta er Success Manager.
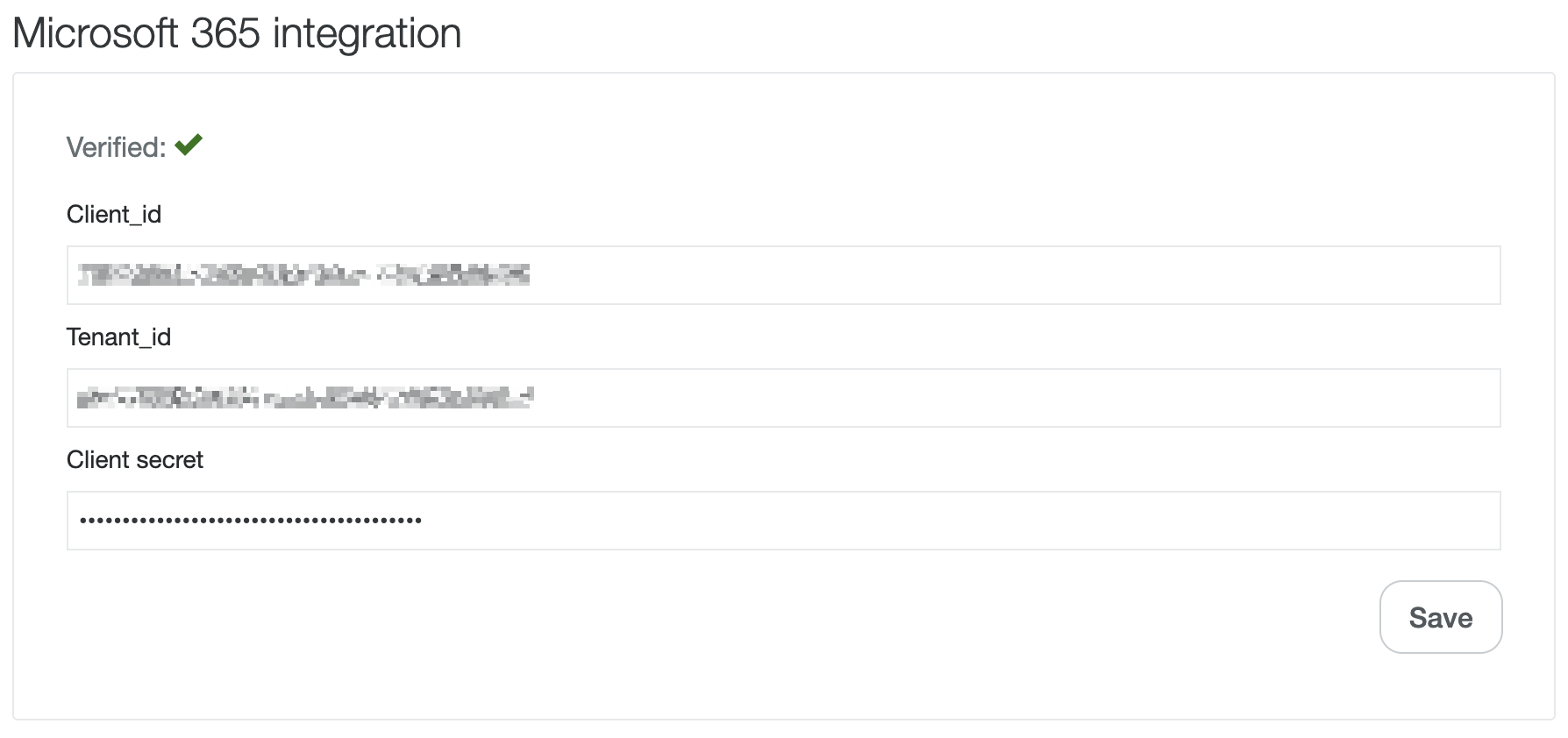
- Fyll i formuläret och klicka på "Spara". Vid det här tillfället kan ett rött kryss visas istället för en grön checkbox - det är ok och kommer lösas genom kommande instruktioner i guiden.
2. Lägg till rättigheter
- Gå till API-behörigheter
- Klicka på Lägg till en behörighet
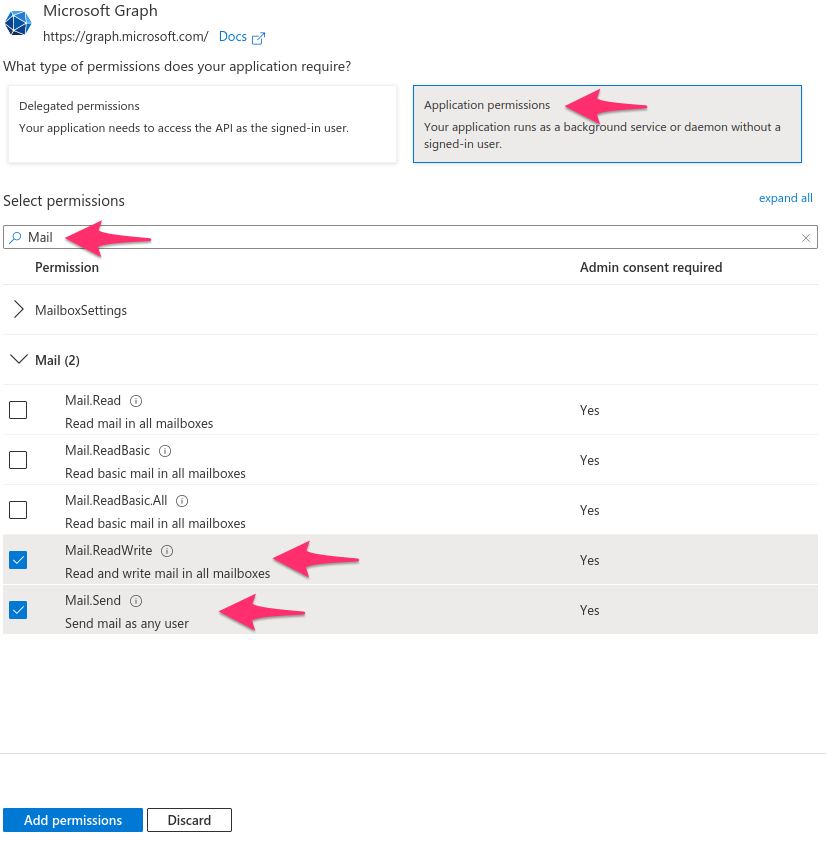
- Välj Microsoft Graph och > Programbehörigheter och sök efter "mail"
- Välj både Mail.Send och Mail.ReadWrite
- Klicka på Lägg till behörigheter
Behörigheten Mail.ReadWrite behövs för att vi ska kunna skicka mail större än 3MB. Vid de fallen kräver Graph API:et att ett utkast skapas före bifogade filer kan läggas till och mailet sedan skickas.
För att bevilja rättigheterna, klicka på Bevilja administratörsgodkännande för <organisation>
3. Lägg till en Appregistreringslogotyp (frivilligt)
Gå till Anpassning och egenskaper och lägg till en Kundologa till Appregistreringen, vilket gör det enklare att känna igen den.

Det går bra att använda följa logo:

4. Add mail-enabled security group
För att endast ge tillgång till de inkorgar som ansluts till Mail behöver ni sätta upp en säkerhetsgrupp som valda konton kan ingå i. Mer information om detta finns att läsa här här.
I Exchange admin center, gå till Recipients > Groups > Mail-enabled security.
Klicka på Add a group och följ instruktionerna i detaljvyn.
Under Choose a group type, välj Mail-enabled security och klicka Next.
Under Set up the basics, fyll enter your details and click Next.
- Vid inställningarna för Assign owners, klicka + Assign owners och välj en ägare i listan. Klicka sedan på Next.
Vid inställningarna för Add members, klicka + Add members och välj sedan de konton som ska användas med Kundo Mail. Klicka sedan på Next.
5. Lägg till Application access policy
En application access policy kan för tillfället endast sättas upp via Exchange Online Powershell. Följande instruktioner beskriver uppsättning av en policy som begränsar applikationsbehörigheter till användarna i säkerhetsgruppen som sattes upp i steg 4. Mer information finns att läsa här.
Anslut till Exchange Online PowerShell. För instruktioner se Connect to Exchange Online PowerShell.
- Skapa en ny Application access policy.
- Ersätt värden på argumenten (AppId, PolicyScopeGroupId & Beskrivning) och kör följande kommando:
New-ApplicationAccessPolicy -AppId <app-id> -PolicyScopeGroupId <security-group-name or email> -AccessRight RestrictAccess -Description <Beskrivning för policyn, t ex `Restrict Kundo Mail app to intended emails`>
- Ersätt värden på argumenten (AppId, PolicyScopeGroupId & Beskrivning) och kör följande kommando:
- Testa den nyskapade application access policyn.
- Kör följande kommando, med Identity och AppId satta till korrekta värden:
Test-ApplicationAccessPolicy -Identity <email> -AppId <app-id> - Test med en mailadress som är med i säkerhetsgruppen ska resultera i AccessCheckResult: Granted, medan en annan mailadress ska resultera i Access Denied
- Observera att det kan ta några minuter innan ändringarna spridits till alla berörda system i M365, varför felaktigt resultat kan visas om testet görs i nära anslutning till uppsättning.
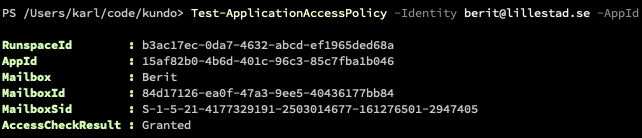
- Kör följande kommando, med Identity och AppId satta till korrekta värden:
6. Aktivera integrationen
Nu kan vi äntligen gå tillbaka till Kundo och inkorgens Inställningar och Skicka & ta emot, där vi bör se en grön checkbox i formuläret för M365-inställningar. Om så inte är fallet kan det bero på följande orsaker
- Access policyn har ännu inte replikerats till berörda system i M365.
- Någon av de tre inställningarna är felinställda. Det är till exempel lätt att förväxla klienthemlighetens id med klienthemlighetens värde
- Integrationen är inställd för en inkorg vars emailadress inte är tillagd till den uppsatta säkerhetsgruppen
Om checkboxen är grön kan ni aktivera integrationen genom att välja Microsoft 365 för inkommande och utgående mail på samma sida:
Om ni har några som helst frågor om uppsättningsprocessen eller problem uppstår, tveka inte att kontakta oss via support@kundo.se.
GDPR
Är ni kund hos oss har vi ett personuppgiftbiträdesavtal tecknat som reglerar hur personuppgifter hanteras.
Detta gäller oavsett vilken integration ni väljer att göra.